I’ve started this blog to help me focus my thoughts and finish projects by way of introducing public scrutiny and some self imposed deadlines. To kick things off I am posting the results of some playing around that I did this weekend with an information disclosure issue in wireless HP printers. To be clear, I am not presenting this as a security issue of significance, but instead just a bit of mental exercise and skill refresh.
A couple of weeks ago while reworking my home lab I had to reconfigure my HP Officejet printer. In the process, I inadvertently printed out a network configuration page. When I went to get it off the printer I found that the last page contained a list of wireless networks in the area, including the BSSID, channel, and signal strength values. This caught my interest as couple of years ago I was inspired by Samy Kamkar’s ‘How I Met Your Girlfriend’ talk at DefCon 18 and I wrote some scripts and a private Metasploit module that would take this same information and query the Google and Skyhook Wireless databases for the physical location of an endpoint. This weekend I decided I would look at the web interface of the printer and see if I could extract the wireless network information from it. What I found was that while the information wasn’t obviously displayed to the end user, the printer did send quite a bit of configuration data to the user’s browser in the form of XML files. About 30 minutes later I was able to use the information in one of the XML files to build a URL that provided the desired information – ‘/IoMgmt/Adapters/Wifi0/WifiNetworks’ .
With this information in hand, I have written a python script that will query a target printer, gather the wireless network list if it exists, query the Google Geolocation database, and display the findings and a Google maps link. The python script, ‘hp.geolocate.py‘, can be found on Github (another new thing for me) at https://github.com/TomSellers/Python.Misc/
Here is an example of the output:
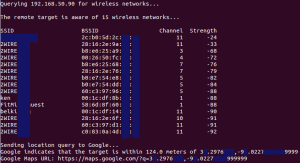
In order to use the script you will need to sign up for a free API key from Google. The process takes about 10 minutes and allows 100 lookups per 24 hours. After the key is acquired, it must be added to the script on line 14 in the variable ‘googleAPIKey’.
The script works on HP Deskjet, Officejet [Pro|Premium], and Photosmart printers. Success depends upon the target device being accessible over IP and wireless enabled. There appears to be no shortage of these. They can be found by searching Shodan for ‘ASIC id’.
In order to provide any value against a preselected target organization, an attacker would have to find a device in his target’s IP range. The device could then be leveraged to determine what wireless and IP networks it was connected to without this script, but the script would provide additional information about the physical location and other wireless networks in range. This additional information may assist with preparations for later on-site efforts.
The printer’s web interface and XML files expose various other information but nothing that would surprise anyone in InfoSec. In addition to printer specs and details you can gather intel on the remote IP networks, fax numbers, etc. On a positive note, none of the XML or HTML documents that I was able to find contained passwords or wireless keys. Typical best practices of not attaching the devices to the Internet (!), configuring HTTPS, and implementing admin passwords will prevent most of the potential risk.
– Tom
Reference:
1. Script download: https://github.com/TomSellers/Python.Misc/blob/master/hp.geolocate.py
2. Google Geolocate API: https://developers.google.com/maps/documentation/business/geolocation/

